Home » VPN Beginner’s Guide – What Is A VPN?
VPN Beginner's Guide - What Is A VPN?
UPDATED March 2026
Advertising Disclosure
![]()
Many or all of the companies featured provide compensation to us. These commissions are how we maintain our free service for consumers. Compensation, along with hours of in-depth research, determines where & how companies appear on our site.
Advertising Disclosure: Many or all of the companies featured provide compensation to us. These commissions are how we maintain our free service for consumers. Compensation, along with hours of in-depth research, determines where & how companies appear on our site.
It’s common for people to see VPNs as complicated software. Many people haven’t even heard of the software before and wonder “What is a VPN?” as soon as they hear its name. They have a hard time getting a grasp over all the things a can VPN do. For others, the inner working of VPNs is still a mystery.
In this article, we discuss what a VPN is and how you can choose the best VPN according to your requirements. Along the way, you’ll also get recommendations to help you choose the VPN that best fits your needs.
You can also look at top-performing services in our best VPN list.

What Is a VPN?
A Virtual Private Network or VPN is a service that allows you to access the internet in a secure and private way. The service does that by redirecting your connection through a secure server and hiding your online actions by encryption.
EXPERT QUOTE
A VPN is one of the most important tools that you need if you use the internet regularly. The technology was designed to help protect internet users from threats such as hacking, as well as help make their internet use as private as possible.

Joel timothy
IT Expert and Tech Writer
How Does a VPN Work?
Alright, right after the introduction and nerdy definitions, we have to take a look at how a VPN works for a user. First of all, you, the user, start the VPN client software on your device. The VPN service encrypts your data before your Internet Service Provider (ISP) has a chance to see it. Not even people connected to your Wi-Fi can see your data.
After getting encrypted, your data goes to the VPN service and from there, to a dedicated VPN server. The server then relays your connection to the online destination you wanted to connect to. It doesn’t matter whether your online destination is a video sharing website or a sensitive banking website. The website will always see your data coming from VPN server location instead of your own location.
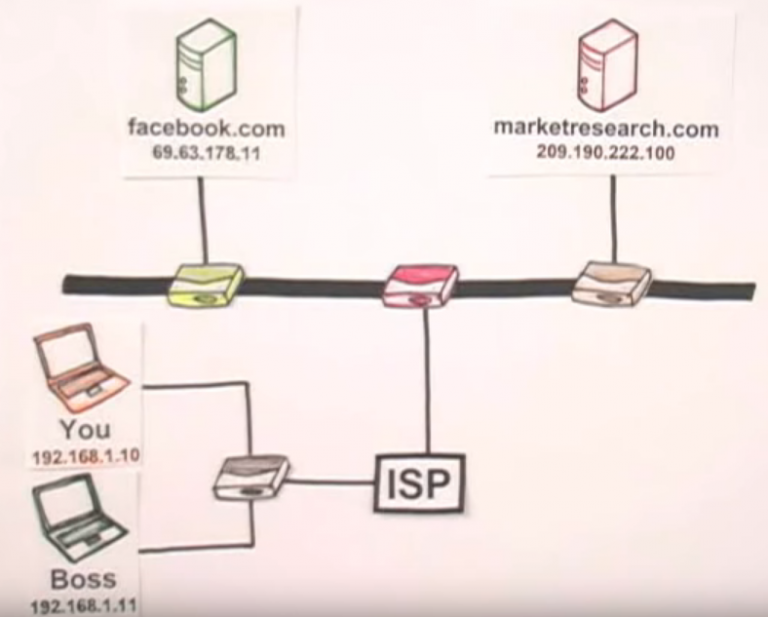
Instead of a bubble cloud, the internet works like a wire. The ones connected to it can access it and distribute it to others that are connected to them. This is how your ISP lets you connect to the internet. In theory, your connection has to go through a secure line. Even your online presence is shown through a public IP not the IP your device has (we’ll discuss this in detail later on).
The data you send out there is open and it’s relatively easy to bypass the security mechanism and peek into your data. In simple terms, the web is a collection of interconnected servers. These servers store websites and serve them to anyone that wants to use them. They talk to each other all the time by sharing information.
These servers can share your information with each other whenever you click on a website to browse it. This may help you surf the internet; however, this isn’t good for your personal privacy.
To understand this further, let us take an example. For instance, you can imagine going online is like taking a commercial flight. However, in this type of flight, everyone from the ticket agent, security personnel, baggage handlers, flight attendants and even pilots take pieces of your data. Your information is thrown around a lot of places when you access the internet.
There’s no issue if someone sees your data while you visit a normal website. However, it’s a different story altogether when this information contains sensitive data like your banking details or your business email.
Though this is the standard, this is not exactly safe. Sometimes, malicious hackers can tap into these connections to see your browser history. Some cybercriminals can go as far as tracking your live location. In other cases, your own ISP can track your online activity and even sell the information to advertisers. This is why connecting to the web without a VPN isn’t 100% safe.
When you connect to the internet using a VPN service, the connection is still goes through your ISP. However, the VPN service encrypts your personal information and the data travels through your internet service to a secure VPN server.
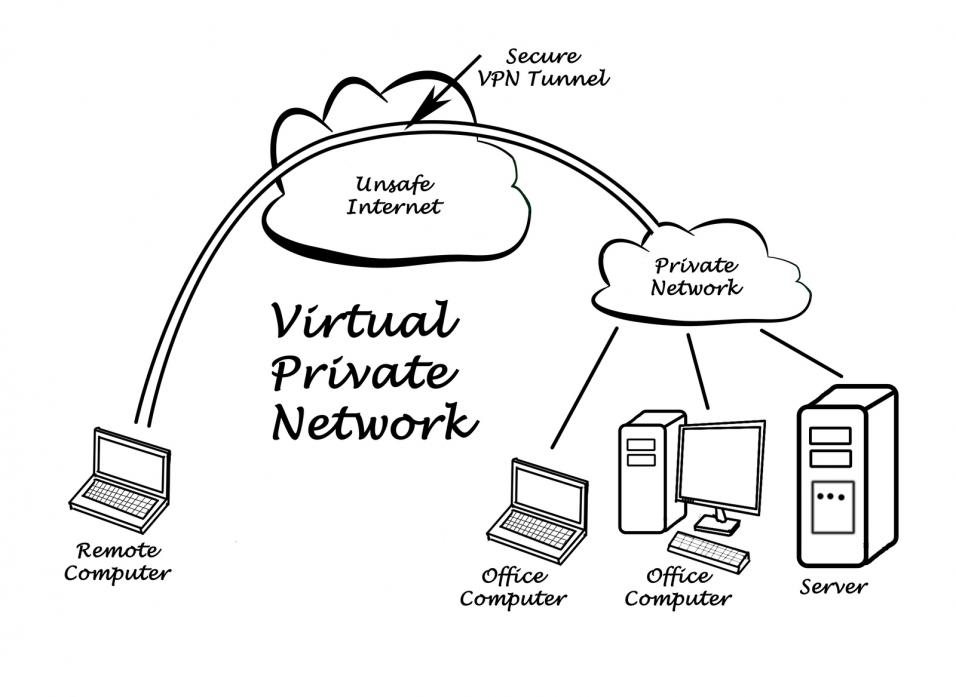
In other words, the VPN server is like a third party that connects to the internet on your behalf. This resolves our privacy and security problems in the following ways:
- The destination website sees the VPN server as the traffic origin instead of you. Even if someone works hard enough to bypass standard security mechanism, they will reach the VPN server, not you.
- No one can identify you or the location of your computer. It’s also much more difficult to pinpoint you as the source of data.
- Your network activity and your browser history won’t get logged either if you’re using a trusted VPN.
- Your data is in encrypted form. So, even if someone is able to peek into your data, they’ll only see encrypted information instead of raw data.
As we discussed above, an internet connection through a VPN service is much safer than standard connections. But how secure can it really get? Read along to find out:
How Secure Is a VPN?
It’s common for IT experts to debate over the extent of security a VPN provides. Moreover, no two providers in the VPN market have identical VPN services, security mechanisms or company offerings. However, there are three main factors that ever VPN service aligns to:
- Legislative limitations of the country a VPN service bases its operations in. The laws of a country where the company servers are located in affect what the types of service a VPN provider can offer.
- The VPN provider’s own policies also affect the way they use their technology or provide service in certain regions.
- The limits of the technology the company uses can also affect the security of their service. It’s possible that a VPN service is still using outdated technology.
To take a closer look at these factors, you can consider the following factors:
VPN Protocols

VPN protocols govern how a VPN service handles your data during transmission. They provide a secure tunnel through which data can get transferred. The most common protocols used are OpenVPN, IKEv2, PPTP, L2TP, and SSTP. Here’s an overview on each of them:
OpenVPN
VPN enthusiasts consider this protocol to be one of the most complete VPN protocols out there. This protocol started as an open source and has improved a lot over time.
OpenVPN has changed hands between hundreds of developers worldwide and each developer has contributed a little improvement to the protocol. As a result, it doesn’t have many of the flaws that other protocols suffer from.
The protocol uses keys known only to the participating users on either end of the transmission. Above all, it is the most adaptable and safe protocol in the industry.
IKEv2
The Internet Key Exchange, Version2 or popularly known as IKEv2 is a protocol developed by Microsoft. The protocol is an improved version of Microsoft’s previous protocols.
This version is much more secure than its previous version. The VPN protocol has the strong support of one of the world’s leading software brands. Microsoft’s premium VPN protocol also provides some of the best security in the industry.
PPTP
Point-To-Point Tunneling Protocol (PPTP) is a tunneling protocol used since antiquity. Developed by Microsoft Pros, it is one of the oldest tunneling protocols in use. The protocol works on old computers and is also a part of the Windows operating system. The protocol is also easy to set up.
However, the protocol is barely secure by today’s standards. A smart hacker will have little trouble exploiting its outdated security mechanism. You should avoid VPN services that only offer this protocol.
L2TP/IPSec
The Layer 2 Tunneling Protocol is a combination of Cisco’s L2F and the old PPTP protocol. While it uses the outdated PPTP protocol, the working behind this L2TP is sound. The protocol uses keys to initiate a secure connection between two users. The connection is secure on each end of the data tunnel.
However, many people don’t consider its execution to be very safe. There have been reports that the NSA was able to break the protocol’s security mechanism to eavesdrop on transmitting data. The IPsec protocol was later included to provide additional security to the existing protocol. Still, it’s safer not to rely on VPN’s that choose this protocol as their primary tool.
SSTP
Secure Socket Tunneling Protocol (SSTP) is another tunneling protocol devised by Microsoft. The protocol establishes a connection using standard encryption techniques such as SSL or TLS. These encryption techniques use a key system that relies on symmetric key cryptography.
While using this encryption technique, two parties encrypt and decrypt data using the same key. This method is quite secure on its own; however, the AES-256 encryption method is much more secure than this method. You should prefer VPNs that offer AES-256 encryption.
Normally, VPN services allow you to choose the security protocol you want to use. The more stable and secure a protocol is, the safer the whole session will be.
However, not all protocols are compatible with every device or platform. Since most of the top-performing protocols are products of Microsoft, they are only usable on Windows PCs. There is limited application of these protocols in Apple devices. For instance, iPhone adopts L2TP/IPsec protocol as its default.
Basics of Encryption
To delve deeper into the world of encryption and cryptography, we’ll see how encryption works. There are three basic steps in every encryption process:
- Taking simple and plan data.
- Applying a secret code (key) to change its form.
- Ending up with hidden and encrypted data.
In the next step, the party that receives encrypted data has to decode it to transform it into readable form. There are two main types of encryption. One is symmetrical while the other is asymmetrical encryption.

In symmetrical encryption, both parties can use the same original key to encode or decode data. Whereas, asymmetrical encryption requires both parties to have different keys for encrypting or decrypting data. Moreover, the encrypting key in this technique is kept public and the decoding key is kept privately.
Typically, VPN services use symmetric encryption techniques. The reason behind that is that keeping private keys for every VPN user out there is inapplicable.
The latest and most advanced encryption mechanism in the VPN circles is the AES algorithm. Understanding these mechanisms need in-depth knowledge of computer science and cryptography.
However, you only have to skim through the surface to know which VPN is better. As mentioned before, VPN services using AES-256 are the most reliable. Top VPNs in our list like NordVPN and UltraVPN use the AES-256 method to encrypt your information.
A VPN can be super secure but all its security comes down to two factors in the end. A VPN can be only as secure as the protocol and encryption method it uses to handle your data.
Legal Constraints and Company Policy
Good VPN companies do everything to protect their user data, privacy and overall security of your online presence. However, these companies are still answerable to the laws of the country they operate in. This factor can affect their service a lot.
Depending on the legislature of a country, a government can coerce the VPN provider to share any information they have. This means that they can be forced to reveal your activity too. Moreover, there are certain international agreements that require VPN providers to share information.
However, if you do research you will be able to find a VPN service that doesn’t base its service in the “14 Prying Eyes”. The 14 Prying Eyes are specific regions that make companies in their jurisdiction liable to share any data they demand. Popular VPNs choose to base their services in such regions. For instance, both NordVPN and ExpressVPN operate from Panama and the British Virgin Islands respectively.
(Note: We are not giving any legal advice. Read it for entertainment purposes only.)
Regardless if a VPN is willing and has the technical capability to keep your information private and safe, it is still answerable to the country it operates in. We can understand this topic in broader terms by following it up with the question below:
Is it Legal to Use a VPN?
It’s difficult to suggest, but in a word, yes.
The concept of a VPN is somewhat new in legal circles. This is why not all countries have proper legislations regarding VPN service. As a result, the rules around VPN use can be murky and judicial institutes can interpret them in many ways.
Overall, most countries allow VPN use, especially countries in North America and Western Europe. However, your physical location matters in this case.
Countries like China, Turkey, UAE, Oman, Iran, and Russia do not allow VPN use as freely. Moreover, other countries like Belarus, North Korea, Iraq, and Turkmenistan outright ban the use of VPNs.
Does a VPN Make Me Fully Anonymous Online?

Does it give you complete anonymity? No. However the extent of anonymity you get is impressive.
Without a VPN connection your browsing data is vulnerable. Everything from your ISP, your Wi-Fi router, or any server you connect can be tapped into to leak your information. A VPN can resolve many of these problems by encrypting your transmission information. It makes your connection appear as if it’s originating from the server, not your computer. You can measure how much anonymity your VPN service provides you based on the following points:
- Is the tunneling protocol and encryption techniques used by your VPN sufficient?
- Does your VPN service keep logs?
- Does the country your VPN operates in force it to keep records on your activity?
- Does the VPN service keep your payment records? Do these records have information that someone can use to identify you?
Not every VPN has the same level of privacy or protection. However, by choosing your connection wisely, you can address the issues mentioned above.
VPN Logging Policies
Some VPNs log specific information related to their users. They might do this because it’s a part of their policy or it might be because the country they operate through forces them. Whatever the case may be, it can significantly affect your anonymity and privacy. The log a provider keeps may include information, such as:
- connection/disconnection timestamps
- IP addresses of the user
- The customers’ activity
- payment logs of the customer
- devices used by the customer
Since your IP changes with each browsing session, these kinds of logs, don’t compromise on your privacy completely. However, an agency can tie those IPs to you if you’re that important to them. To be safe, you should choose VPN providers that keep fewer logs on its users. Still, a VPN with zero log policies is ideal.
However, many VPN services market themselves as being completely protective about your privacy. Yet these VPNs don’t have zero log policies and keep some type of data. To see what data they keep, you should read their privacy policy.
There are VPN providers that state incomplete information in their privacy policy. Some of these services say that their country doesn’t bind them to retain user information but fail to mention their company’s data retention laws.
Difference between Free and Paid VPN Services
Having a comprehensive VPN service requires a strong financial backbone. A good VPN service needs to have a vast network of robust servers, considerable infrastructure, and numerous employees. Moreover, maintaining high-end servers all around the world adds up expensive operational costs.
You shouldn’t forget that nothing is ever given for free. So, if a VPN service is offering their service for free, you need to be wary about the things you’ll have to compromise on. Are they allowing you free access so that they can log your activity? Are they doing it to run ads on your device or are they selling your data to a third party?
A paid VPN service doesn’t demand a pocket-denting investment from you. There are many great solutions available for as little as $3-7 per month. This doesn’t seem much, considering that you’ll be able to access a secure connection, free of ads and data tapping third parties.
How Much Does a VPN Cost?
On average, VPN cost around $4.99 a month. However, VPNs exceeding the cost of $10 a month are not uncommon. Choosing pricier alternatives over cheaper ones doesn’t make much difference if you are choosing any top-tier VPN.
Many VPN services hand out huge discounts to users who choose long-time subscriptions. In other words, if you opt for a one or two year subscription instead of a monthly one, you can get a reasonable deal.
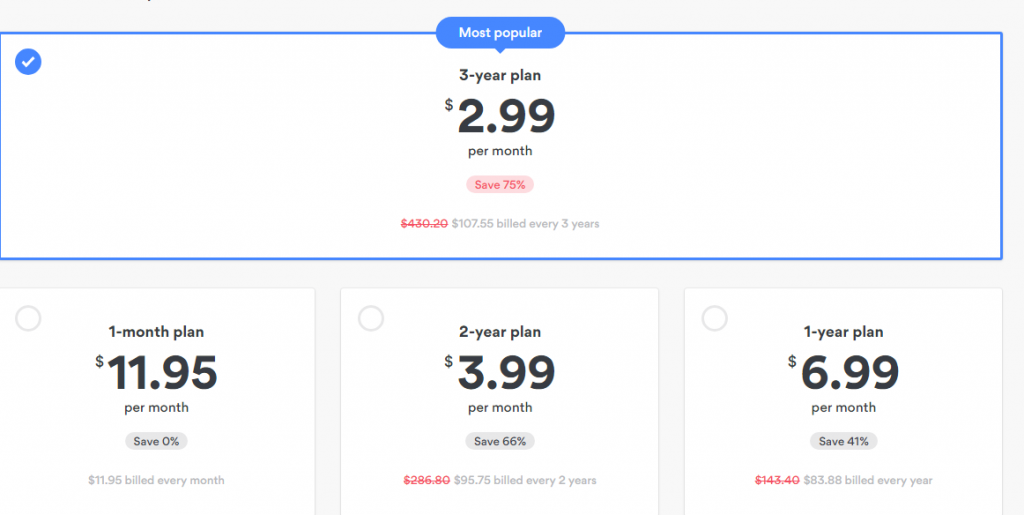
For instance, NordVPN costs $11.95 per month, but costs $3.99 per on a two year subscription. NordVPN goes a step further and lowers it price to $2.99 per month on a three-year subscription – which is a 75% discount on the actual price.
Can I Use a VPN for Torrenting?
For a one-word answer, yes you can. However, a lot depends on the kind of service you’re using and also the type of material you’re torrenting.
Torrenting is a special type of file-sharing. People torrent files through a special protocol to distribute huge files across a number of people simultaneously. Despite torrenting being frowned upon by many authorities, the service is perfectly legal if you have the rights for the file you’re sharing. However, piracy of data is illegal regardless people are using torrenting or any other medium for it.
VPNs have differing policies regarding their tolerance for torrenting. Some VPNs like Norton VPN by Symantec, disallow torrents or other P2P services. Yet, most VPNs have open support for torrenting. You can avail torrenting through popular VPNs such as NordVPN, SurfShark and ExpressVPN.
However, there is another aspect of offering torrent services. A VPN service may log torrent-related data. If a user is utilizing torrenting for illegal file-sharing, they can get traced and caught by agencies using this data. Still, if a service has a zero-log policy, then it won’t log torrent data anyway.
Can a VPN Be Used to Watch Netflix or Other Streaming Sites?
Yes it can be. But not all VPNs can do this.

Many people use VPNs to access region restricted content. Websites like Netflix and iBBC Player have restricted access for certain shows or TV series’. This is because certain license agreements allow various TV stations to have rights over content. It also means that services like Netflix can sometimes face problems while hosting their own shows on different platforms.
Streaming services block their content in some parts of the world using location filters. VPNs can free you from web of legal complications and let you access region-restricted content. VPN users can watch restricted content by redirecting their access through a foreign server. Ideally, the users have to connect to a server in the country where the restricted content is available.
Do VPNs Work on iOS or Android?
Many top-tier VPN services offer mobile applications for their services. In the end, it all goes down o the simple rule of supply and demand. If a certain company is popular enough that there is sizable demand for its mobile-phone version, then the VPN service will probably develop a mobile application for their service.
ExpressVPN, NordVPN and SurfShark offer Android versions for their VPN service.
How Can I Install a VPN on My Router?
The most convenient way to let several users benefit from a VPN connection is by installing a VPN on your router. You’ll no longer need to install a VPN service on every single device you use. Any device connected to your router will be able to take advantage from a secure connection.
The first step is to make your router compatible with VPN services. You can do this by visiting the website of the manufacturer of the router. In most cases, Tomato-boosted and DD-RT Flash Routers can work fine with VPNs.
However, each service may require different steps to set up the VPN. It’s possible that your router-provider has a separate section to teach their users how to set up VPN on their routers.
For most devices, the installation process is simple and straightforward. All you have to do is to log-in to your router and fill in a couple of easy forms.
How to Use VPN & TOR Together?
Have you ever heard of the term overkill? Well, using a VPN and TOR web browser is something similar to that. Though, VPNs and TOR are different things, you can use them in cohesion for paramount security and online privacy. To understand how this happens, you can read the points below:
Though, the TOR browser may seem similar like VPN itself, it’s quite different on its own. It gives you the ability to access the internet by routing your connection through different nodes. For added security, the browser encrypts your connection once on each node. The best thing about this browser is that it’s completely free.
However, you’ll have to compromise on lower speeds on the TOR browser. To use your VPN service and TOR together you only have to follow two basic steps:
- Turn on your VPN connection like you normally do. After this all your connections go through the VPN service.
- Open the TOR browser and connect to it. Experience a completely private and secure internet connection.
Again, the only problem with accessing the web through this extra-secure channel that your internet speeds will slow down quite a bit.
Kill Switches & IP Leaks
Kill Switches
A kill switch is a feature that some VPN services offer. It ends an internet access immediately once the encrypted connection drops. This helps to prevent any privacy vulnerability before it arises.
IP Leaks
IP leaks are a nightmare for many users that uses VPNs for safe and private access to the internet. If your device or VPN connection is suffering of an IP leak, it means a hacker or malicious website can extract your real IP from your device or network connection.
However, IPs leaks are not always the VPN’s faults. They can arise from your web browsers and even from your reliable OS. Top-tier VPNs have advanced features that prevent different types of leaks in your VPN.
For a more comprehensive explanation, you can read our guide on various VPN Tests and Checks – how can you fix them.
Protect yourself from hacking and surveillance with 256-bit AES encryption, DNS/IPv6 leak protection, kill switch, and split tunneling.
High speed, ultra secure, and easy to use. Instant setup.
Advertising Disclosure
![]()
The information we provide you is free of charge and a result of extensive research by our product experts. We use affiliate links in our site that provide us with referral commissions. While this fact may not influence the information we provide, it may affect the positioning of this information.
When You Should Use a VPN?
- To encrypt your online activity on internet.
- To hide your online activity from anyone who wants to see it.
- To hide your location and see region-restricted content such as Netflix, Hulu and iBBC Player.
- Make yourself more anonymous on the internet.
- Stay protected when connected to public Wi-Fi.
Protect Your Internet Browsing
GET NORD VPN NOW!

98%
OVERALL RATING

Advertising Disclosure
The information we provide you is free of charge and a result of extensive research by our product experts. We use affiliate links in our site that provide us with referral commissions. While this fact may not influence the information we provide, it may affect the positioning of this information.
CONTENTS
- What Is a VPN?
- How Does a VPN Work?
- How Secure Is a VPN?
- VPN Logging Policies
- Difference between Free and Paid VPN Services
- Can I Use a VPN for Torrenting?
- Can a VPN Be Used to Watch Netflix or Other Streaming Sites?
- Do VPNs Work on iOS or Android?
- How Can I Install a VPN on My Router?
- How to Use VPN & TOR Together?
- Kill Switches & IP Leaks
- When You Should Use a VPN?