Home » Online Privacy For Journalists – The Ultimate Guide
Online Privacy for Journalists - The Ultimate Guide
UPDATED February 2026
Advertising Disclosure
![]()
Many or all of the companies featured provide compensation to us. These commissions are how we maintain our free service for consumers. Compensation, along with hours of in-depth research, determines where & how companies appear on our site.
Advertising Disclosure: Many or all of the companies featured provide compensation to us. These commissions are how we maintain our free service for consumers. Compensation, along with hours of in-depth research, determines where & how companies appear on our site.
Surveillance and censorship are increasing all over the globe. Technology has allowed surveillance to become much easier than it previously was and governments are exploiting it to isolate journalists and censor them.
People are finding indications of George Orwell’s famous book “1984” in their own countries. Many journalists fear for their safety when they think of exercising their right to freedom of speech.

It’s not uncommon for oppressive regimes to punish people for raising their voice for what they think is right. Some countries jail, torture and even execute journalists if they don’t support their propaganda. However, the hazards of repression are not limited to third-world countries and controlling regimes.

Dangers to freedom of speech are spreading over the Western Hemisphere like a dark cloud. People expect their Orwellian fears to rain down upon them soon.
It is shocking to see a serving president ban media access to his conferences. He does that because he thinks believes that former president is spying on him. We even hear sitting presidents to label the media to be the country’s biggest enemy. So it isn’t surprising when veteran journalists get bombarded over the mention of Watergate.
The memories of President Nixon refresh with every new tweet brandishing media persons as enemies and traitors. Even Republican Senators like the late John McCain voiced concerns over the future of democracy.
Recent news on intelligence agencies like the CIA leads us to believe that these agencies can become dangerous when they’re adamant to probe you. They can even crack the strongest of layer encryption if they’re determined to do so. Journalists fear for the freedom of the press because they know censorship is the first step that leads to a dystopian world.
However, it is still possible for people to save their emails, call and texts from interception or at least make them really difficult to crack. They can make the life of these infiltrators much harder if they take measures to protect their sources.
Ensuring the safety of data, the anonymity of sources and protection of your privacy requires a degree of effort. You should be ready for any threat, be it spying or hacking of your electronic devices. Even promises of “I won’t reveal my sources” don’t count for much if you’re not careful about protecting information on your computer. NSA contractor, Edward Snowden and interviewer Toni Loci can testify that after the complaint against the former.
So, what can a journalist do to ensure their data is secure and their sources don’t get compromised? This article presents a detailed guideline to online privacy for journalists.
Brushing the Basics
The first step you can take to secure yourself is by limiting your attack surface. What this means is that you have to minimize your use of devices and applications as much as you can. Any apps that you install on your device have to be from trusted sources and must require minimal rights to your device functionality. You also have to make sure that your system security is completely patched from all sorts of leaks and is up-to-date.
A user has to isolate their devices along with their environment. For instance, they should keep their computer in an isolated and physically insulated place when they’re checking for files. It is also not wise to use unpaid software because more often than not these applications collect your data in exchange for free service.
Users have to cautious both in the digital and real-life environments. These preventions aren’t related to software as they are to common sense. For instance, a journalist should never type the name of their source, especially not in any app or file of your computer. Entering that sort of information in a file on the cloud is a cardinal sin when you’re safe keeping resources.
EXPERT QUOTE
Online privacy and information technology are two interactive units. It is the advancement in technology in the first place that has threatened personal privacy and reduced the amount of control we all have on our identifiable data. Today’s technology is driven by Big Data which allows collections of huge amount of data and then the use of data mining technology to find patterns.

Steve Ongaro
IT Expert and Tech Writer
Protecting Sensitive Data & Communicating with a Source
After getting done with the basics, you should look for more measures to secure communication with your source. Moreover, a journalist has to be careful about sensitive information too, because any exposure of that data can have grave consequences for both the journalist and the source. Journalists can act upon the following steps to save themselves their sources:
Protect the Data on Computer
Decrypting a regular password doesn’t take much. However, irregular passphrases are a lot harder to crack. These passphrases are generated as random combinations of letters or words.
Still, experts refer password managing tools for added protection of your passwords. You can choose any security tool like KeePassX, LastPass or 1Password. In such cases, you’ll only need to remember one password instead of a bunch of them.
However, when you use services like email, you shouldn’t lend much trust to password managers, just be sure that you don’t forget your original password.
Experts on information security like Arjen Kamphuis, recommend a simple but useful way to protect data on your computer. You should ensure that your password is longer than 20 characters. Yes, the longer a password is, the harder it is to crack. However, it is significantly harder to remember such long passwords too.
You can choose random and easy to remember password phrases like “T|-|1sAh@c|<n0TaRe@|_pA$s\/\/0rD” to secure your device or account. To test the strength of your password, you can visit Gibson Research Corporation’s password checker.
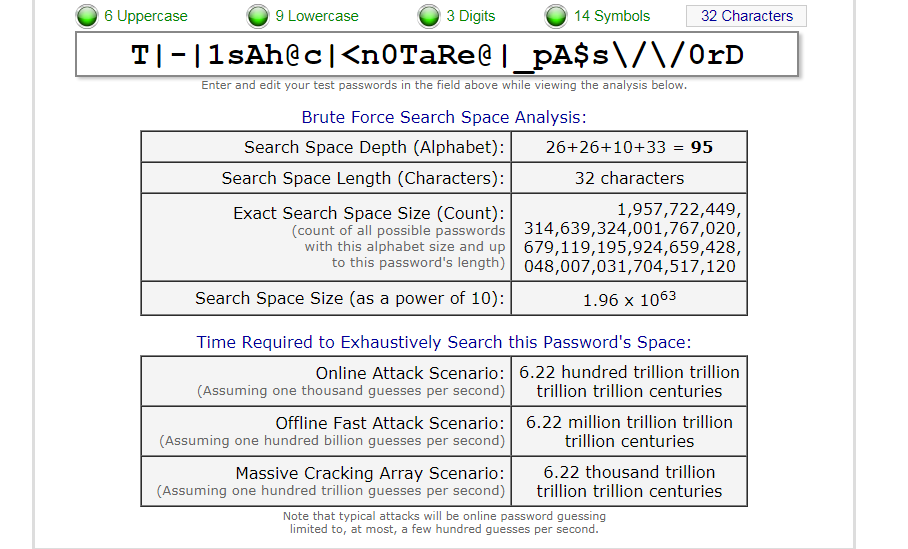
You can also get creative and try out your favorite lines of poetry to estimate how good they can be as passwords. This is how well it fairs against Shakespeare’s famous work of play:
“To be, or not to be: that is the question: Whether ’tis nobler in the mind to suffer. The slings and arrows of outrageous fortune, Or to take arms against a sea of troubles, And by opposing end them?”
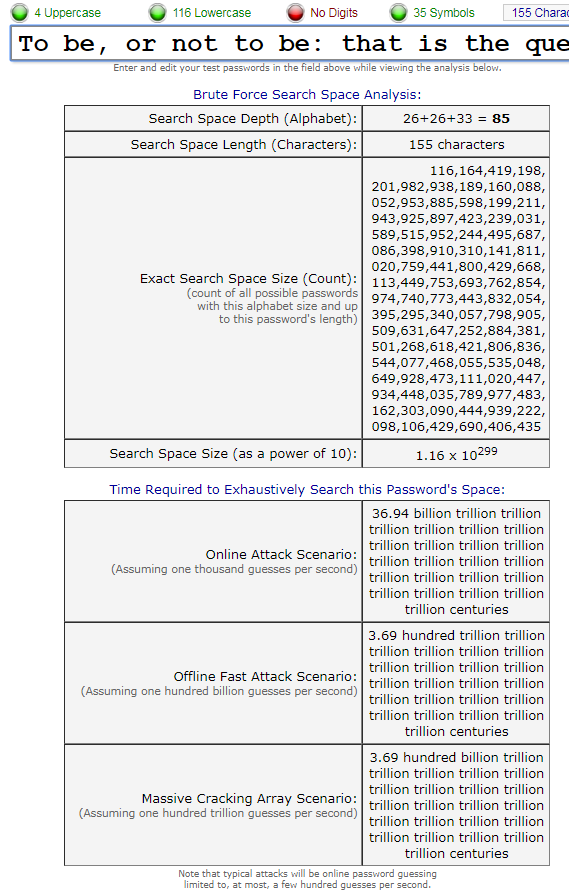
As you can see from the screenshots from the GRC website, a pass phrase is a lot stronger than a fully fledged traditional password. A complex sequence of characters, even when coupled with symbols is no match for the aesthetic work of Shakespeare.
Full-Disk Encryption
This mechanism helps to keep your data safe if anyone gets his hands on your phone or data. Applications like VeraCryptor, FireVault and Bit Locker can ensure that your device has full-disk encryption.
However, if you put your device to sleep instead of shutting it down, it can be vulnerable to attacks even after full disk encryption. You can follow this guide from Micah Lee to encrypt your laptop.
Avoid Chats on Phone
Phone companies are famous for storing data related to caller and receivers’ numbers. They also save the location and the time these calls are made. In the US (as well as several other countries), laws require these companies to reveal information on registered calls.
To be safe from this, privacy experts recommend the use of a secure call service like the Signal app. In these types of software, both the caller and receiver need to have the application installed. You can get an idea on how to use it following this tutorial.
You can communicate with your source as much as you want but be careful of bringing your phone to sensitive meetings. To ensure a secure connection, you would have to buy a device for the sources as well and tell them in advance the number they have to contact.
Make sure the device you buy is disposable so you or your source isn’t tracked later. You can also get tracked through your cellular network signals. This is why; it’s wiser to use these applications to make their job a lot harder.
If anyone fails to implement proper measures for privacy, they can catch that person by looking at the footage of the place you met with their source.
Going for Secure Messengers
Like your calls, your texts can also get intercepted. Once someone gets their hands on your message, reading from it will be easier than reading something from a sign-board. Journalists have to make sure that they use messengers that have end to end security.
Though applications like Telegram and WhatsApp have this kind of encryption, they already been compromised once. However, developers claim that they have fixed this issue. Some experts suggest that applications like SMSsecure and Therena.
These applications use the signal protocol which is also implemented by WhatsApp, Facebook Messenger and Google Allo. However, these signal-level encryption features in Facebook Messenger and Google Allo are not there by default but exist as an optional service.
Tor Messenger is the extension of TOR – the world’s most secure web browser. You can choose their service to benefit from the most advanced level of chat security there is.
As some cybersecurity experts suggest, having encrypted text isn’t enough sometimes. Encrypted text constantly being exchanged between two users is an alarming sign for anyone that monitoring traffic. So make sure that you’re running your traffic through a reliable source.
It’s also advisable to never forget deleting your texts after the conversation is done. It’s a useful thing to remember to save your phone if falls into the wrong hands. However, forensic scans can still detect information by tapping into the registry directory of your device.
Payment Method
Pay through a method that is difficult to trace back to you. It’s ideal to use cash in most situations. However, as long as the other part is interested, you shouldn’t hesitate using cryptocurrency as well.

Cryptocurrency is a great way to pay for services anonymously and it’s almost impossible to know your identity if you use it wisely. Still, you have to keep in mind that the value of cryptocurrency can fluctuate and it can be costly if a currency shoots down. To understand how to utilize cryptocurrency, you can take a look at this guide from Business Insider.
Avoid Well-Known Names
In most cases, it’s safe to assume that big corporations have back-channels to security services, especially if they originate in the US or the UK. This list of exploiting software can even include big names in the operating system industry.
Befriend Hackers
Keeping in touch with hackers gives you more than good company. Having friends in the hacking community lets you stay updated on the latest threats and trends in cyber security. It also helps you to avoid technological blunders that can land you in hot waters.
Avoid Using Organizational Chats
Organizational chat forums like Google Hangouts, Slack, Campfire and Skype are not meant for private conversations. Hackers can break into these applications without much effort. Moreover, they can are open to exposure in the event of a disclosure request from the court to solve legal issues at your workplace.
This is why; it’s essential that you avoid them when you’re talking to sources. Even conversations between colleagues and editors have to be outside these applications when you’re conveying private information. You have to protect the identity of your source at all costs.
When conveying information with your colleagues or editors, you can choose services like Jitsi. This application has built-in functions that are similar to functions in Skype and are a viable option to replace it.
Blackphones
If you want to go over the charts, you can think of using blackphones. These phones are perfect for political dissidents and whistleblowers who are sharing extremely classified information. Blackphones enable users to surf the web, make calls or send text messages or emails.
Though blackphones are perfect replacement of regular phones, they can also get tracked through IMEI numbers. So, you need to use it with an RFID signal-blocking bag.

Encrypt Everything
Understanding the importance of this security measure is fairly easy. The higher the cost decrypting your data is, the harder it will be for agencies to able to tap on you. If you weren’t involved in a major leak like Edward Snowden, Julian Assange or Chelsea Manning, it’s unlikely that agencies will expend much effort cracking strenuous encryption algorithms for you.
Even if someone is adamant on tracking you, it’s difficult to crack tunneling protocols like OpenVPN and PGP. People trying to break strong encryption algorithms like AES-256 will find themselves in a real grind. However, having failure-free security requires more than encrypting your transmitting data with AES encryption.
Two-Factor Authentications
Two-factor authentication is also an effective way to secure your data. When you have a two factor authentication installed, you’ll have to enter your password. Once you enter the password, you’ll receive a code on your number via text message.
Tools like Yubikey and hardware token helps secure confidential files on your computer. To have an in-depth read on the topic, you can take a look at 7 golden rules for password security.
However, buying those laptops online is not a great idea. It’s better to buy them second-hand from a shop and pay only through cash. You should also remove all sorts of connectivity from the machine such as Wi-Fi, Ethernet, modem or Bluetooth.
Educate the Source
In the end, we’re all human; our sources can make mistakes too. It’s even possible that the even leave a trail of evidence behind them. Once you get your hands on the information it’s important that you teach your source how to hide that information. Being able to store the information and communicating it through a secure channel should be your ultimate goal.
It’s important that the source relays the information in a safe and secure manner. You should also educate the source to use secure devices to transfer the information to you. In many cases, people don’t understand how they have to handle sensitive information. While other times, sources don’t know what precautions they should take when they’re acting as sources for sensitive information.
It’s useless to have a secret source if that person is transferring information through an iPhone while you use an air-gapped and secure laptop.
Use Secure System to Receive Files
It’s necessary to have a secure system to share files across the internet. However, using emails isn’t a bright idea. Make an account on file-sharing websites but limit privacy on the files that you receive there.
Options like Dropbox or Google Drive might be good for personal use but can’t be relied upon for sensitive information. It’s better to use something that is less popular but is more secure. Platforms like SecureDrop allow you to receive files from anonymous sources. Moreover, you can also check the contents of the file through a safe and secure environment.
The famed NSA contractor, Edward Snowden is still on the run from US officials and has asylum in Russia. He recommends terms Dropbox as “hostile to privacy” instead, he suggests using SpiderOak. However, you can also use OnionShare if you want to transfer files in a secure and safe manner.

Say No to Notes
While it may be against your journalistic instinct, keeping notes can be destructive for your source’s security or your own. You should avoid keeping notes whether it’s in your laptop, phone, calendar or anywhere else. If any trace of the source’s name, phone number, email, or initials gets in the hands of the wrong people, the situation can worsen a lot.
Avoid Cameras
It’s important that you travel in public transport when you’re on your way to a secret meeting. Your source too, must use public transport to avoid suspicion. Moreover, you should avoid popular malls or any place where there can be a security camera.
Say Goodbye to Social Media
When you’re job is exchanging sensitive information that can lead to life or death scenarios, you ought to be very careful. Top journalists and reporters like to stay under the hood and don’t have any full-blown public accounts on social media websites.
Dealing with information demands you to be anonymous and be able to disappear when you need to. Having a social media account stops you from doing that. Instead of leaving information by deactivating your account, you should delete such accounts permanently.
Dedicate a Computer to Scan Suspicious Files
USBs are prone to carrying viruses, spyware or malware like mosquitoes carry Malaria. Email links and file attachments also distribute malware and cybercriminals use them often to infect unsuspecting users.
Experts recommend using air-gapped computers to isolate these threats. You can use that computer to plug in USB’s and download files from the web. However, you should be wary of plugging in a USB from that computer to your regular computer because air-gapped computers only quarantine threats.
Using a Secured Computer
Information Security professional Arjen Kamphius suggests buying an IBM ThinkPad X61 or X60 (pre-2009) is a good option. He regards the as the only modern laptops which can replace low-level software.
How to Be Anonymous Online
Secure communication and the protection of confidential data are not the only things a journalist has to face. It’s essential for them to avoid being tracked when they’re online. A person’s online activity can tell a lot about what they’re doing.

Likewise, if someone is able to track a journalist’s online activity, they can make sense of what that journalist is doing. People can use this to blow the steam off your story. In worse cases, your online activity can lead authorities to your source. To ensure safe and private surfing you should consider the following tips:
Use Incognito Mode
The incognito mode (or private browsing mode) is one of two ways through which secure browsing is possible. Many people use it when they don’t want their online history to get stored in the web browser.
It allows the user to surf through the internet with a fair amount of anonymity. Your family won’t be able to look at your online history. Moreover, it stops websites from gathering data of your profile through HTTP cookies. Other basic tracking technologies used by advertisers are also restricted when people browse in the private mode.
However, if your work needs to be more security than an average user does, than this method shouldn’t be used. Your IP can still get tracked even when you’re in private mode. Hackers can even tap into your ISP to know about your identity and location.
Switch between Alternative Browsers
Using alternative browsers for surfing is another good trick to try. You should try to switch between web browsers such as Comodo Dragon or Dooble . These types of browsers have limited capabilities but make up for that by focusing on user privacy.
Even by deleting cookies, you can have relative safety. Cookies are not delicious pieces of biscuits that most people assume. For web browsers, cookies are pieces of code that monitor your activity when you visit a website. These codes are there either to improve the functionality of the website or used by advertisers to gather information about the type of content you see online.
Turning off the location settings in the browser may not do much but at least hides your exact location. Using CCleaner to wipe off cookies is good but it still doesn’t offer you encryption when you’re online.
The TOR Browser
Experts regard TOR to be the most secure web browser available in the market. It was initially developed by the US Navy to operate in a closed network. People can use it to carry out private communications and or to set up websites without showing yourself.
The web browser is available at its website: TorProject.org. The best thing is that it’s free of cost and anyone can use it after downloading it from the website. It’s extremely difficult to monitor activities once you start using the TOR browser.
The web browser’s advanced level of encryption, encodes your information once at each node it passes through. The only drawback it has is slow speed which is there because the browser operates on several layers of security. The web browser also relays connection randomly along with encrypting it which makes tracking you near to impossible.
Change Operating System
Like the TOR browser, there are operating systems that are dedicated to privacy. One such operating system, Whonix acts like a gateway for the TOR browser. The only lets you access websites that is inside TOR’s networks and has TOR users on it. You can contact with your source through such websites to ensure anonymity.
However, there is another TOR-based OS that is much more popular. The Amnesiac Incognito Live System or “Tails” encrypts all information. People even think that the legendary Edward Snowden admires this software.
Alternate between Search Engines
Google is the most popular search engine in the world. However, it is also the browser that saves the most information about you. If Google is your favorite web browser, you can disable this setting by signing into your account and deleting history in the browser.
However, this is not recommended. You should prefer a web browser that doesn’t gather information on its own. Web browsers like DuckDuckGo let you browse the web without being monitored continuously.
Clear Short-Term Memory
Your DNS cache can sometimes store data to optimize your web experience. Yet it isn’t safe if you’re trying to be completely off the radar. You can learn simple commands to delete the information in DNS caches through your operating system.
Likewise, HTML web storage allows the web browser to store information. However, it’s different from cookies and is difficult to trace and remove one by one. It usually runs by default, so you can turn it off in Internet Explorer and Mozilla Firefox. For chrome, you need to consider add-ons to handle this matter.
Use VPNs!
Signing up to a VPN is the first step to any privacy strategy. For a detailed outlook on VPNs, check out our VPN Beginner’s Guide – What is VPN?
VPNS are ideal for browsing the internet in a safe and secure manner. There are free VPNs available but using them for privacy would be suicidal. You can check the list of best paid VPNs and select the one that fits your need.
Though these VPNs are designed for privacy and security, only a few offer uncompromising safety on the web. So, you should keep in mind considerable factors before choosing one.
All VPN providers offer advanced encryption that lets you access the internet anonymously. It’s near impossible for anyone to track your movements. You can also view the content and websites banned in your region through a VPN.
Because a VPN lets you access the internet using a remote server, it’s hard to trace your location. However, even if your connections drops, features like kill-switch stop your connection from getting exploited from malicious parties.
For journalists, the most important feature of a VPN is zero-log policy. If the VPN is able to log your information, you can get in trouble. It’s also important that you dvise your surce to use VPNs for secure access to the internet.
Repairing Leaks
VPN is a great way to ensure your privacy on the web. However, it still isn’t 100% safe. The VPN an suffer from leaks that can end in getting you caught. However, you can work around that problem by reading our detailed article on VPN tests and checks – how to fix them?
Advertising Disclosure
The information we provide you is free of charge and a result of extensive research by our product experts. We use affiliate links in our site that provide us with referral commissions. While this fact may not influence the information we provide, it may affect the positioning of this information
Protect yourself from hacking and surveillance with 256-bit AES encryption, DNS/IPv6 leak protection, kill switch, and split tunneling.
High speed, ultra secure, and easy to use. Instant setup.
How Can Journalists Secure Their Emails?
It’s really difficult to ensure security for your email. Companies that provide users emails to use don’t hesitate to share your data if the government demands. You can secure your email through the following steps:
Safe Extensions
The simplest way to ensure that you and your source are safe when using common web mails like Google or yahoo is to install plug-ins like Mailvelope. Your source should also do the same to make it work.
The plug-in encrypts and decrypts emails as they come and go. Gmail has a similar extension known as SecureGmail. This service also performs encryption and decryption on emails in such a way that Google can’t decrypt them (or so the company claims).
Secure Email Providers
Email services like Hushmail and Kolab Now provide enhanced security than most networks. However, Hushmail can be powerless ifa court order directs it to share information with the government. Still, you can use Kolab Now because it is in the jurisdiction of Switzerland and is relatively safe (unless you want to hide from the government of Switzerland).
Disposable Email Addresses (DEAs)
People use DEA when they need a temporary email. They are deleted after they are used. The most common use for these emails is when people need to sign up for service without being spammed later.
However, security isn’t its strongest feature. Still, you can use services like Guerrilla Mail and Mailinator with TOR browser to use them safely.
Encrypting Emails
Encrypting web-mails isn’t that much easy. You have to copy and paste your messages in text windows and scramble and unscramble them through encryption software like PGP. However, the Mozilla Firefox email app – Thunderbird is also a reliable contestant.
Avoid Simple Mistakes
This is perhaps the first rule in email security. Users should be careful of opening unknown links to avoid phishing attacks. These attacks are carried through by malicious files that contain harmful code.
Watch out for misspellings in the sender section of the email. It is also not uncommon for these dangerous files to pose as the email of someone you know. These attacks may seem innocent but cost a lot to your security and privacy.
Parting Advice
Your system can get comprised through various different ways so you have to be vigilant all the time. Once your system gets hacked, you can get almost nothing. Prevention is the best way to do your job in a safe and private manner.
Protect Your Internet Browsing
GET NORD VPN NOW!

98%
OVERALL RATING

Advertising Disclosure
The information we provide you is free of charge and a result of extensive research by our product experts. We use affiliate links in our site that provide us with referral commissions. While this fact may not influence the information we provide, it may affect the positioning of this information.
2 thoughts on “Online Privacy For Journalists – The Ultimate Guide”
Nowadays, it is incredibly difficult to obtain privacy on the Internet and that is why your guide is very useful and incredibly important to me.
Thank you for your comment. We are happy that we could help.
Regards,
Marija, VPNVanguard